With rising threats of cyber-attacks and security breaches, there is an urgency within companies to protect their virtual borders by updating Information Technology (IT) and Operation Technology (OT) systems. Assessing the infrastructure landscape in each facility creates an overarching understanding of your OT systems that need protection against cyber threats that negatively impact line equipment or shut down your manufacturing facilities.
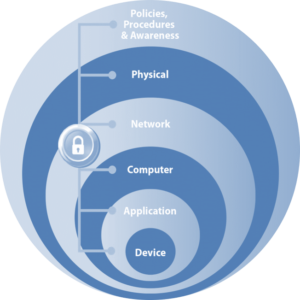
Securing industrial assets requires a comprehensive security model based on a well-defined set of security policies. Protecting industrial assets requires a “defense-in-depth” security approach that addresses internal and external security threats. This approach utilizes multiple layers of defense (physical and electronic) at separate industrial levels by applying policies and procedures that address different types of threats. For example, multiple layers of network security protect networked assets, data, and end points, and multiple layers of physical security protect high value assets. No single technology, product, or methodology can fully secure industrial networks.
Recommendations and best practices for securing manufacturing assets:
- Deploy holistic security based on “defense-in-depth”
- Conduct a security risk assessment
- Develop a manufacturing security policy that supports manufacturing operation requirements based on enterprise security policy best practices
- Implement a manufacturing network security framework to establish domains of trust and appropriately apply security policies
- Establish a IDMZ between the Enterprise and Manufacturing Zones
- Prevent traffic from traversing the IDMZ
- Use application mirroring within the IDMZ to converge Manufacturing and Enterprise Zone information
- Harden computers and controllers
- Utilize industry standards such as ISA-99



